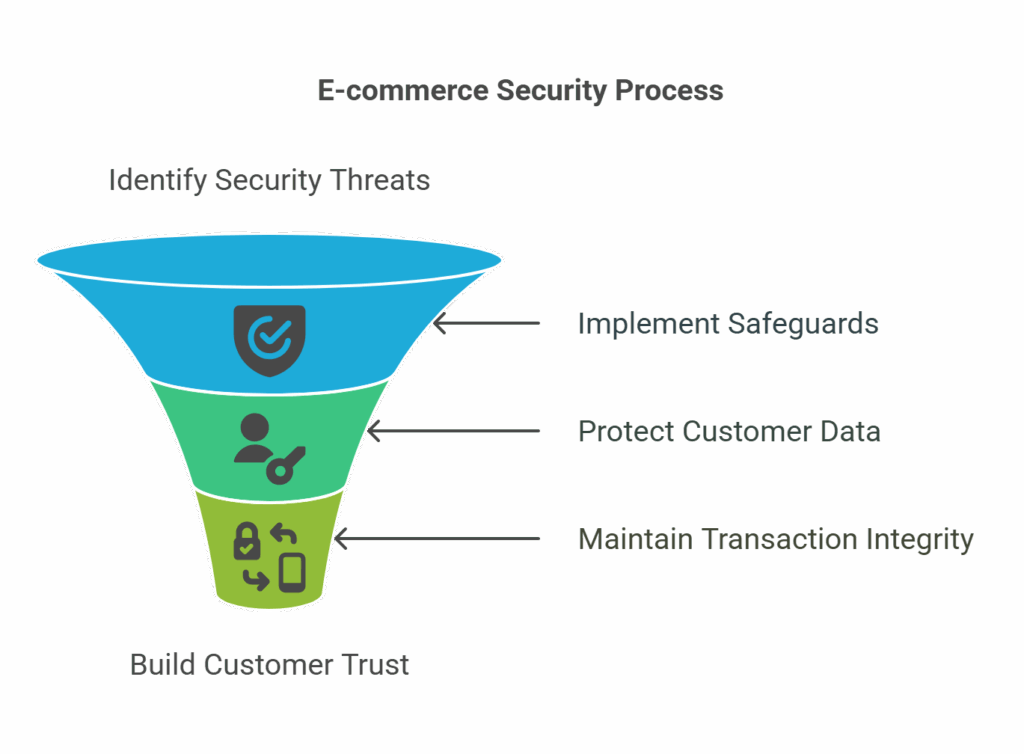
In today's digital world, e-commerce security best practices are more important than ever. It's not just about protecting payment details—it also involves securing customer information, user accounts, and the integrity of every transaction. With cyberattacks becoming more frequent, recognizing potential threats and putting strong safeguards in place can significantly reduce the risk of data breaches.
Security lapses can lead to serious consequences. Businesses may face financial losses, legal issues, reputational harm, and a breakdown in customer trust. Personal data such as names, addresses, and payment information can be stolen and misused, causing lasting damage for both customers and companies.
Understanding these risks highlights why strong security is not optional but essential. Knowing what’s at stake helps pave the way for applying the right e-commerce security best practices to protect your store and maintain customer confidence.
This section will explore common security threats and introduce practical methods to help you secure your e-commerce operations effectively.
Implementing SSL Encryption: The First Line of Defense
SSL encryption is a fundamental part of e-commerce security best practices. It protects sensitive data as it travels between a user's browser and your website server, ensuring that information remains encrypted and confidential. By using SSL certificates, businesses can prevent hackers from intercepting customer data during online transactions.
More than just a security tool, SSL builds trust. When customers see that your website is secure, they’re more likely to feel confident entering payment details and completing a purchase. Without SSL, browsers often display security warnings that can drive customers away and negatively impact sales.
Setting up SSL is one of the simpler steps in improving security. Many hosting providers include SSL certificates, and installation usually takes just a few minutes. Despite its simplicity, the security and trust it offers are significant.
Incorporating SSL into your store is one of the most effective e-commerce security best practices to protect your customers and strengthen your business credibility.
Ensuring Access Control with Role-Based CRM Systems
Role-based access control (RBAC) is a practical approach to managing who can access different types of data within your organization. Not every team member needs full access to all information. By applying RBAC in CRM systems, businesses follow e-commerce security best practices by ensuring employees only view the data relevant to their roles. This reduces the risk of internal data leaks or misuse.
RBAC enhances overall security by keeping sensitive information restricted to the right people. For example, customer service teams might need contact details but not financial data. With RBAC, permissions are assigned according to job functions, minimizing the chances of unauthorized access.
This method also boosts efficiency. Clearly defined roles help employees locate and use the information they need without unnecessary distractions. It keeps your CRM system streamlined and easy to manage.
Additionally, RBAC supports compliance efforts. Structuring access in a controlled way helps meet data protection regulations, which is critical during audits or when adhering to privacy laws.
Using RBAC is one of the e-commerce security best practices that not only protects your data but also improves internal operations and ensures your business remains audit-ready.
Two-Factor Authentication: Enhancing Account Security
Two-factor authentication (2FA) is a powerful tool for strengthening account security. It requires users to provide two forms of identification before gaining access to their accounts. This added step significantly reduces the chances of unauthorized access, making it one of the e-commerce security best practices businesses should prioritize.
Most 2FA setups combine something the user knows, like a password, with something they have, such as a one-time code sent via SMS or an authentication app. Even if a password is compromised, the second verification layer blocks intruders from getting in. This makes 2FA a reliable method to guard against data breaches and account takeovers.
Setting up 2FA on e-commerce platforms is usually simple. Many platforms already offer built-in support for it, allowing quick activation without major technical challenges. Customers benefit too, gaining peace of mind from knowing their accounts are better protected.
To apply this effectively, businesses should start by enabling 2FA for admin users, then extend it to employees, and finally offer it to customers. This phased rollout secures the most critical access points first, gradually strengthening overall platform security.
Incorporating 2FA is a practical and essential step in following e-commerce security best practices, helping protect sensitive data and reinforce customer trust.
Secure API Integrations: Protecting Data in Transit
APIs, or Application Programming Interfaces, are essential for e-commerce. They allow different systems to communicate smoothly, joining together various components of your platform. But if these API integrations aren't secure, they can become weak spots that hackers target.
To protect data in transit, businesses need to prioritize secure API practices. One key step is using HTTPS protocols for API calls, ensuring that data transferred is encrypted. This encryption helps block unauthorized parties from intercepting and reading sensitive information.
Another best practice is authentication and authorization. Ensure your APIs authenticate users and verify requests before granting access. Limit API access to specific IP addresses and use tokens or keys for added security.
Regular monitoring and audits are also important. Set up systems to track API activity, looking for unusual patterns or potential threats. By keeping an eye on these integrations, you can catch and fix any security risks quickly.
Secure API integration can significantly enhance the safety of your e-commerce operations, ensuring data stays protected as it moves from one system to another.
Regular Data Backups: Preparing for the Unexpected
Regular data backups are a critical component of e-commerce security best practices. They ensure your business can recover important information in the event of a cyberattack, system failure, or technical error. Having a reliable backup system helps minimize downtime and keeps operations running smoothly.
Consistent backups prepare your store for unexpected disruptions. By securely storing copies of your data, you can restore information quickly and reduce the risk of long-term loss. This can protect your reputation and save you from potential financial setbacks.
There are several ways to automate data backups. Cloud-based services are especially popular, offering automatic and scheduled backups with little manual work. These services typically update in real-time or at regular intervals, giving you confidence that the latest data is always safe. Local backups, using external drives or internal servers, add an extra layer of protection and offer faster access during internet outages.
A good backup strategy outlines what to back up, how often it should happen, and where the data should be stored. It's also important to test these backups regularly to confirm that they can be restored when needed.
As part of e-commerce security best practices, regular data backups provide a safety net that helps your business stay resilient and prepared for unexpected challenges.
Building Secure, Cost-Effective Custom CRM with Fuzen
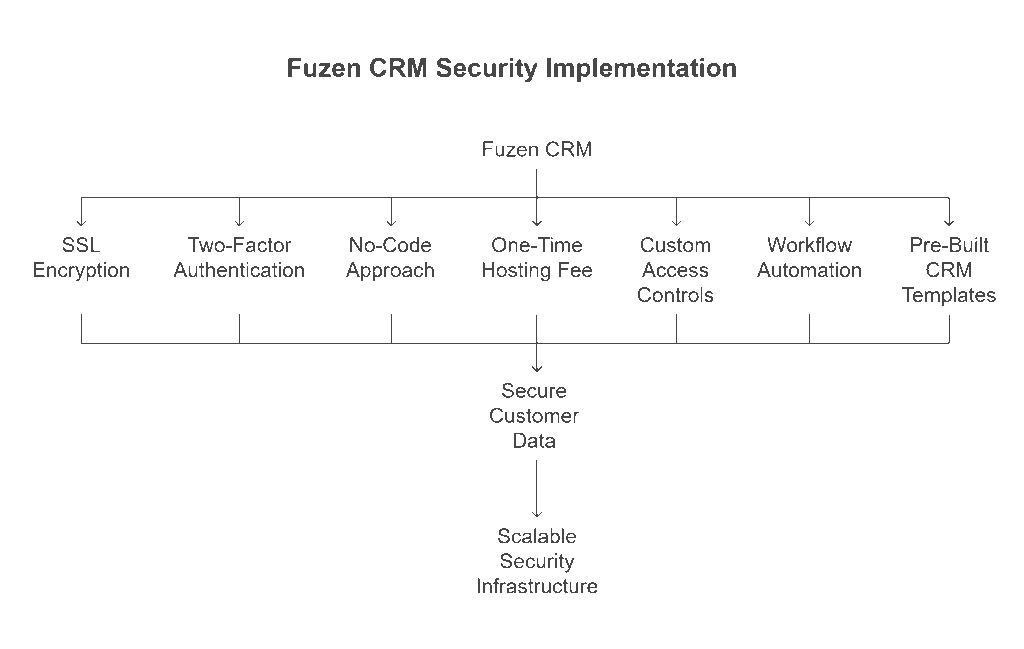
Bringing all these best practices together, Fuzen offers a practical way to build a custom CRM solution that aligns with top e-commerce security best practices. From SSL encryption to Two-Factor Authentication (2FA), Fuzen enables you to implement strong security features seamlessly into your CRM workflows.
One of the major advantages of Fuzen is its no-code approach. You don’t need a technical team to build or maintain your CRM. With intuitive drag-and-drop tools and AI-driven customization, you can configure a system that matches your business needs while ensuring tight security.
Fuzen also offers a one-time hosting fee model, removing the burden of expensive recurring subscriptions. This makes it ideal for startups and small businesses that want enterprise-grade security without stretching their budgets.
The platform supports custom access controls, role-based permissions, and workflow automation, which help enforce security policies efficiently across your team. Whether it’s securing customer data or managing internal access, Fuzen’s features make it easier to stay compliant and protected.
Additionally, Fuzen provides pre-built CRM templates that include standard security configurations, helping you get started quickly without compromising on protection. Its architecture is built for scalability and flexibility, so as your business grows, your security infrastructure grows with it.
Fuzen ensures that implementing e-commerce security best practices is not only achievable but also affordable and sustainable. For businesses looking to protect their operations while staying agile and efficient, Fuzen offers the tools and support to make it happen.
Conclusion
Implementing strong e-commerce security best practices is no longer optional—it’s essential for protecting customer data, maintaining trust, and ensuring business continuity. From SSL encryption to role-based access control and regular backups, each layer plays a vital role in securing your online store.
Fuzen empowers businesses to put these practices into action with ease. It's a no-code platform that allows you to build a custom CRM tailored to your specific security needs. With features like 2FA, automated workflows, and centralized data management, Fuzen ensures your e-commerce operations stay secure, scalable, and cost-effective. For any business serious about growth and data protection, Fuzen provides the tools to do both efficiently and affordably.

Pushkar is a seasoned SaaS entrepreneur. A graduate from IIT Bombay, Pushkar has been building and scaling SaaS / micro SaaS ventures since early 2010s. When he witnesses the struggle of non technical micro SaaS entrepreneurs first hand, he decided to build Fuzen as a nocode solution to help these micro SaaS builders.